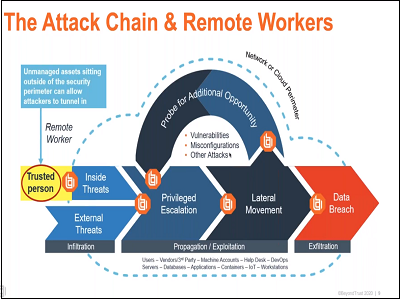
Security Strategies to Enable the Remote Workforce
Sensitive data and data privacy
Shadow IT and free, or consumer-grade, tools
Bring your own device (BYOD)
Secure remote access – the foundation for effective remote working
Read more...